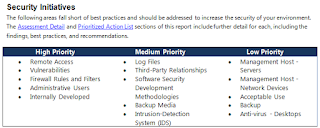
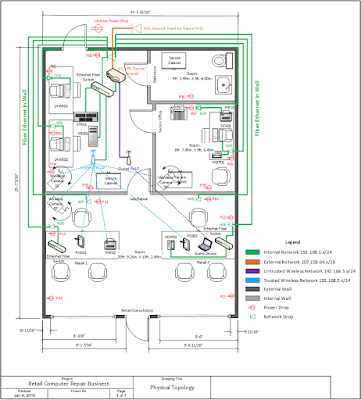
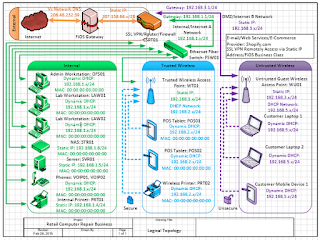
Hardware
- RackSolutions: Need help finding the perfect rack for your equipment? This is a good place to start.
Software
- PortQuiz.net: Ever find yourself inside an organization and were not sure if they were blocking a particular port? What about your own ISP? This nifty little site has all their ports open. Simply follow their instructions and you can test to see if a particular port is being blocked locally. Cool stuff.
- DownDetector.com: Want to know if a particular website is down? Check out this site. They track a lot of different sites. Unfortunately, they do not track my own but hey, not everybody is perfect. Or maybe, my site is always up so there's no reason to track mine? Regardless, it can be useful when you are trying to figure out some of your Internet issues you may be facing.
- Ultimate Boot CD: Do your work on computers? If so, there is often a need to boot to something else in order to look at the hardware in an unbiased way and/or take a look at the data on the hard disk safely. UBCD is a great tool for this. It allows you to work on a computer separate of the OS that is already loaded. Very handy.
WayBack Machine: Wish there was an archive of the Internet; a way to look at how web sites looked in the past? There is! The WayBack Machine! Pretty cool tool. - Social Media:
- HootSuite: This is a great site for managing multiple platforms. You can schedule posts which is nice, especially when you are trying to plan things out in advance.
- Klout: Another nice site for posting across social media platforms AND it gives you a social media index score to give you an idea of how influential you are.
- Buffer: Another site for posting and scheduling posts across various social media platforms.
- Hastagify: Looking for the perfect hashtag? This is the site for your. Insert a search term and it will give you various hashtags associated with it.
- Have I been Pwned? Great site for finding out if your personal information has been compromised. Interesting fellow (Troy Hunt) created this out of some research he was doing and we are the lucky benefactors. Check it out!
- troyhunt@hotmail.com
- https://plus.google.com/+TroyHunt/posts
- https://twitter.com/troyhunt
- https://www.facebook.com/troyahunt
- SpeedTest. How fast is your Internet connection? Stop taking your service's declared speed as fact. Stop taking their technical support's word for it. Check out SpeedTest which will test both your upload and download speed.
- Network Management Tools
- Hacking:
- Kali Linux: If you are interested in ethical hacking, penetration testing, etc., this is where you need to start. Great bootable disc that comes with all kinds of tools for testing an organization's defenses.
- Cybrary: This is a great little site. They provide quite a bit of technical training FOR FREE! Of what I have gone through so far, it is fairly well done (better than my stuff) and fairly high level meaning it should be easy for most people to digest as it is not overly technical. But, it is a GREAT way to get exposed to a lot of technical topics. Great job guys!
- Hack This Site: Develop your ethical hacking skills. This is a great site to learn about hacking. They have progressively more difficult projects as well as discussion boards where you can discuss hacking. Of course, you should only do this in an ethical manner to better learn how to defend your systems.
- Hacking Tutorial Tips & Tricks: Tips and tricks to learn about hacking. Please use responsibly.
- EvilZone Hacking: Discussion board where you can read and learn about hacking from hackers.
- AnyWho:
- Yansi:
- Metasploit. Want to learn about penetration testing? Metasploit is a professional pen testing tool. There is also a "limited features" version that is free, where you can start to develop some of your skills.
- MX ToolBox. Test your or someone else's DNS or SMTP servers. This tool can help you determine if you have been placed on a blacklist, have DNS errors, as well as other problems.
- External IP Addresses. Need to determine your external IP address? These tools can help with that.
- Tor: The Onion Router. Want anonymity? Give this browser a shot. Be sure to read about. You can be virtually invisible on the Internet.
- PC Part Picker. Want to build your own system? A little unsure about all the components you might need? Let this site help you make sure you have accounted for everything you need.
- CSS Validator. Want to know if you CSS is valid and follows all the appropriate rules? This is the site for you. It shows you any problems you have and helps you correct them.
- XHTML Validator. Want to validate your XHTML? This is the site for you. Much like the CSS Validator, this site well help you improve your XHTML.